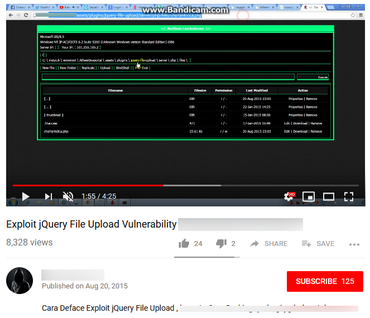
D3c3mb3r hackers exploit ThinkPHP flaw to hack thousands of Chinese websites

ThinkPHP flaw to hack thousands of Chinese websites A hacker group named D3c3mb3r has been found exploiting the vulnerability in the wild. Another hacker group was also found exploiting the vulnerability to infect servers with the Miori malware. A bug in the ThinkPHP framework has left over 45,000 websites open to a barrage of attacks. Hackers have been exploiting the bug to gain access to web servers. A hacker group named D3c3mb3r has been found exploiting the vulnerability in the wild. Another hacker group was also found exploiting the vulnerability to infect servers with the Miori malware. According to the attacks began after a Chinese cybersecurity firm, VulnSpy, posted a proof-of-concept (PoC) of the exploit for ThinkPHP on ExploitDB - a popular website that hosts free exploit code. The PoC points out that by exploiting the vulnerability, attackers could execute malicious code on the underlying server. "The PoC was published on December 11, and we saw internet-wide scans le...